How Scammers Are Using Your Face to Commit Fraud
Key Takeaways
- Gold Pickaxe is a smartphone malware targeting facial data for scams.
- Scammers use stolen faces for deepfakes and bank hacking.
- Stay cautious of app permissions, avoid downloads from fake sources, & enable 2FA for added security.
How cautious are you about how your face is used on the internet? If you’re not, you should be.
Now is a good time to start, as there’s a new strain of smartphone malware called Gold Pickaxe designed to harvest your face data, all so it can be used as part of a scam.
What Is Gold Pickaxe?
As reported by Bleeping Computer, Gold Pickaxe is a malicious mobile app first spotted by security firm Group-IB, forming part of a much larger and sustained malware campaign called Gold Factory. Gold Pickaxe is usually disguised as a legitimate app to trick people into downloading it; it’s considered an iOS Trojan or Android Trojan.
To boost the number of people downloading the app, Gold Pickaxe’s operators send out social engineering emails impersonating government officials. The email typically pushes the user to download the fake app. In the reported example, the app was disguised as a digital pension manager using a page impersonating the Play Store, the Android app store.
How Does Gold Pickaxe Work?
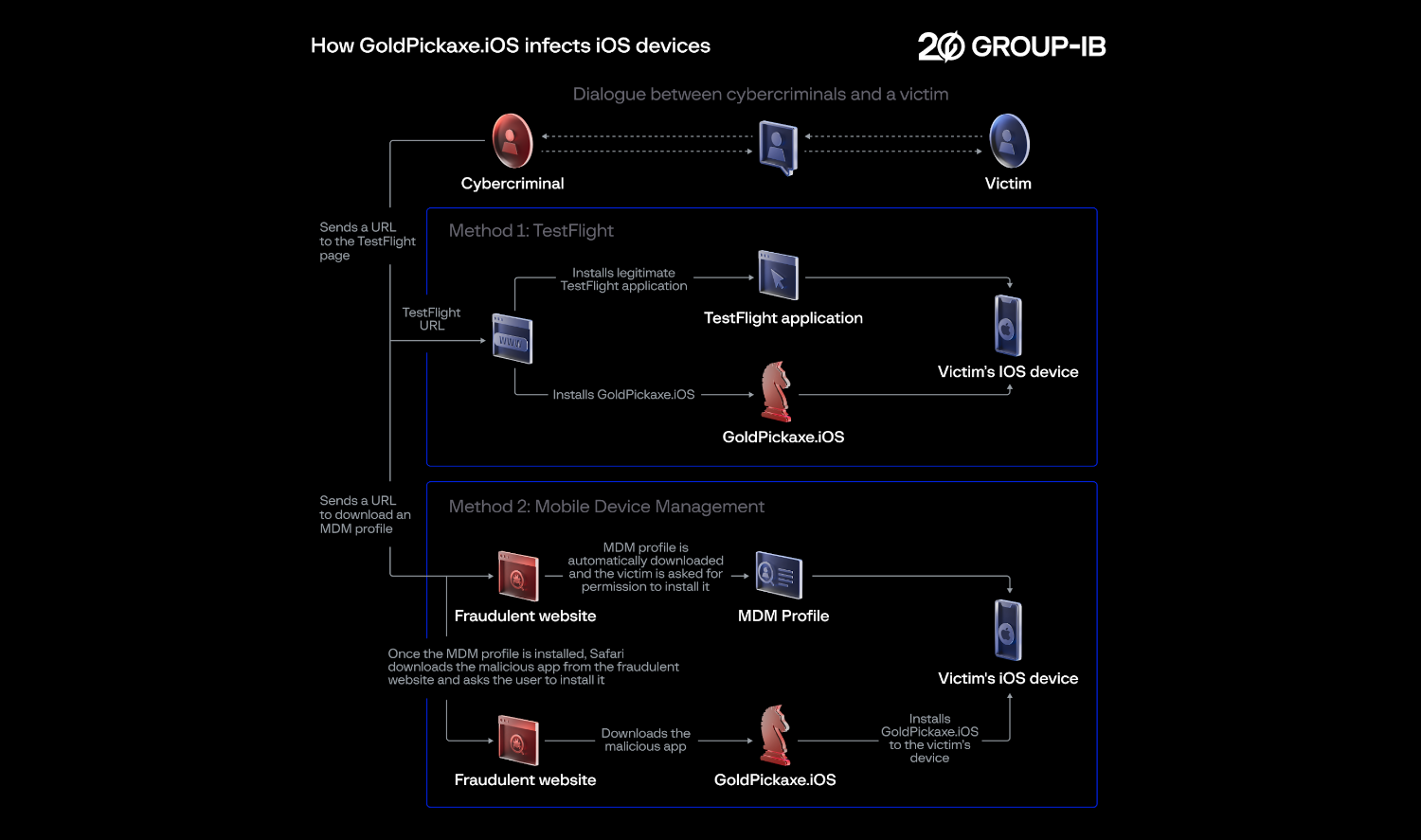
Once the victim downloads the infected app onto their phone, it immediately starts gathering data on the user. This includes going through text messages, scanning web traffic, and looking through files. As part of the social engineering, victims are pushed to install a Mobile Device Management (MDM) profile. Once installed, the Gold Pickaxe malware operators have almost complete control over the device, as an MDM grants access to features such as remote wipe, device tracking, application management, and much more.
However, they cannot steal banking information immediately, and what separates Gold Pickaxe from other malware strains is its main goal. It will try to get a picture of the victim’s face, which it can achieve through one of two means.
The first is by directly asking the user to scan their face. This is why Gold Pickaxe usually takes the form of a government-backed app, as it’s not uncommon for these apps to ask for a face scan through the phone’s camera. When the user goes to log their face through the app, it grabs the data and sends it back to the scammer. Another more advanced variant of the malware, Gold Pickaxe
The second is by indirectly stealing the victim’s face data. In some strains of Gold Pickaxe, it will intermittently take a photo through the front-facing camera in hopes that it will catch your face. If it can’t do that, it can instead send over the photos saved on your phone to see if they contain your face.
As per Group-IB:
GoldPickaxe.iOS
is
the first iOS Trojan
observed by Group-IB that combines the following functionalities:
collecting victims’ biometric data
,
ID documents
,
intercepting SMS
, and
proxying traffic through the victims’ devices
. Its
Android
sibling has even more functionalities than its iOS counterpart, due to more restrictions and the closed nature of iOS.
It’s important to note that the malware does not get biometric face data from services like Face ID. Instead, it tries to photograph your face through the camera or within your files.
What Can Scammers Do With Your Face?
It may seem odd that a scammer would try to get a photo of your face, but there are plenty of reasons why a scammer would seek it out.
Gold Pickaxe harvests facial data to help hack bank details. Some banks won’t allow users to send a large sum of money without a face scan, so grabbing the victim’s facial data allows scammers to avoid that limitation.
However, it’s by no means the only way a scammer can use a picture of your face. We’re seeing a rise in convincing deepfakes that allow people to make a fake version of someone say whatever they want. These deepfakes can then be used to perform more scams.
Finally, if someone is trying to steal your identity, your facial data is a good place for a scammer to start. With it, they may take out loans and create official documents under your name. The scammer will need a little more data than a name and a face to do this, but given how Gold Pickaxe sends over a ton of data, it’s possible for a scammer to pick out key bits of information from it.
How to Stay Safe From Face Scanning Attacks
As scary as Gold Pickaxe sounds, it greatly depends on someone believing the initial email and downloading the app from a fake website. As such, always do not download apps from suspicious sources, and learn how to protect yourself from social engineering attacks.
When installing an app, make sure to read all of the permissions. If an app that doesn’t need to see your face or surroundings asks for camera permissions, treat it with caution. You can also install an antivirus app to keep these malicious apps off your system. Also, on Android devices, don’t sideload apps, especially ones you don’t know or trust or can’t research or inspect where they came from.
And if you’re worried because there are a lot of images of your face on the internet, see if you can activate more defenses on your sensitive online accounts. For example, if your accounts support two-factor authentication (2FA), enabling it will add another layer of defense that a scammer needs to breach before they get into your data, and it’s really easy to set up and use.